Monday, June 27, 2011
UID in Nandurbar district: fails to meet milestone
Will UID dream become a REALITY?? (FreshNews.in)
Kumbhar first wrote to Tera Software on February 22. In the letter, he complained about project coordinators’ shoddy job. He sent another missive on April 1. “I have reports that eight units have been fitted in Nawapur, but only three are working. The official representatives of your company do not communicate with tehsildars,” he stated.It's all about people.
Chicago air pilot pilot program at O'Hare
Opinions still clash on effective safety measures (WGN)
Crucial takeaway:
"We would define a photograph in the category of a biometric,'' said Steve Lott, spokesman for the Air Transport Association, which is collecting the pilot data from airlines and making it available to the TSA. "It's certainly not to the degree of an iris scan or a fingerprint, but we would say a photo can serve as a clear identifier of a person in combination with the information in the database."There's a lot going on here. If they can't make the system work better for a very small fraction of all air travelers, the ultimate frequent flyers, there is little hope for an improved process for ordinary air travelers.
The exclusion of concrete biometric validation, however, concerns some lawmakers.
Crucial takeaway:
But biometric ID validation can be implemented at approximately the same cost as less-secure methods, according to officials at a company that was involved in testing in 2008 with Southwest Airlines pilots at Baltimore Washington International Airport.
Friday, June 24, 2011
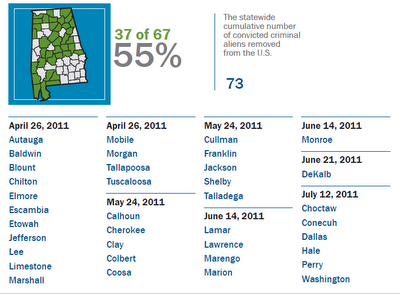
DeKalb County Alabama joins Secure Communities
DeKalb County joins federal immigration program (Sand Mountain Reporter)
DeKalb County is shaded light gray. Other Secure Communities counties are darker gray. The red lines represent major interstates in Alabama.
I started this map on the theory that counties would be more likely to adopt Secure Communities if they (a) bordered a county that was already participating or (b) were located on an interstate highway. Both are the case with DeKalb county.
DeKalb County also borders the state of Georgia and its northern tip appears to be within a few miles of Tennessee. Law enforcement jurisdictions that are located on interstates and near two (or more) other states face significant challenges.
See also: Alabama joins Secure Communities
UPDATE (November 15, 2011):
I've fallen behind in keeping track of the Alabama counties participating in Secure Communities. Thankfully ICE has provided an up-to-date resource for where Secure Communities is in place. Here's Alabama:
Here's the pdf with Secure Communities participation for each state.
The DeKalb County Sheriff's Office is the most recent addition to the U.S. Department of Homeland Security's Secure Communities Initiative.
 |
| Click to enlarge. |
I started this map on the theory that counties would be more likely to adopt Secure Communities if they (a) bordered a county that was already participating or (b) were located on an interstate highway. Both are the case with DeKalb county.
DeKalb County also borders the state of Georgia and its northern tip appears to be within a few miles of Tennessee. Law enforcement jurisdictions that are located on interstates and near two (or more) other states face significant challenges.
See also: Alabama joins Secure Communities
UPDATE (November 15, 2011):
I've fallen behind in keeping track of the Alabama counties participating in Secure Communities. Thankfully ICE has provided an up-to-date resource for where Secure Communities is in place. Here's Alabama:
Here's the pdf with Secure Communities participation for each state.
India ID spurs development
It is important to realize that India's UID effort is an institution building project.
A unique individual identity establishing each individual Indian as a legal entity is a necessary precondition for the country's development.
The Aadhar platform intends to offer a unique identification for every citizen (Times of India). But its utility extends beyond identification, as it will potentially enable citizens to gain greater access to public services and empower the marginalized to seek their rights.Not only will it enable greater access to public services, which is obviously a good thing. It is perhaps far more important that it will enable access to private services. Try getting a loan without a legally recognized identity. One can't even write a check (spend your own money with more efficiency and security) without one.
A unique individual identity establishing each individual Indian as a legal entity is a necessary precondition for the country's development.
Biometrics + Smartphones = Greater Privacy
Biometrics will prove far more useful in protecting privacy than undermining it.
This Press Release extolling the virtues of "The Awesome Motorola Atrix" provides another example of how this is the case.
This Press Release extolling the virtues of "The Awesome Motorola Atrix" provides another example of how this is the case.
Thursday, June 23, 2011
Loss prevention, ROI and fried chicken
A large Popeye's franchisee has implemented a fingerprint system that tackles two identity management challenges: time-and-attendance and rights management.
Popeye’s franchisee adds fingerprint readers to reduce fraud (QSRweb.com)
Popeye’s franchisee adds fingerprint readers to reduce fraud (QSRweb.com)
In addition, with fingerprint biometrics, employees cannot "borrow" a manager's card for transaction authorizations, which increases the assurance that a manager has followed the proper business and loss-prevention processes. Also, cards and passwords are easily lost, stolen or forgotten, which can be expensive and time-consuming to replace.
Modality and adoption, a disinterested techie's point of view
There's a lot going on in this piece by Alex Daley, a technologist who has done some rather interesting things.
It's possible he confuses the retina and iris modalities, and the body of the piece doesn't describe any sort of "onslaught" but the piece is still worthy of consideration.
The Coming Biometrics Onslaught (CaseyResearch.com)
It's possible he confuses the retina and iris modalities, and the body of the piece doesn't describe any sort of "onslaught" but the piece is still worthy of consideration.
The Coming Biometrics Onslaught (CaseyResearch.com)
Tuesday, June 21, 2011
Wales: End free school meal stigma with biometrics
All pupils would pay for meals with fingerprint (BBC)
Granted, you can shield children from knowing who receives a free meal without using biometrics. Any number of card configurations could manage that. It turns out, however, that card-based solutions among children end up being very expensive in time and money because of lost and forgotten cards.
*30% - assumes nearly all of a schools population qualifies for a free lunch and that there is still a social stigma even when nearly everyone is in the same situation. If only half of the students qualify, which is not uncommon in the United States, the Welsh numbers suggest that 15% more students will eat with an anonymous system than would eat in its absence.
Ms Watson said: "68% is the average take up of free school meals where we have a system that identifies against a near 100% where we have a system that doesn't identify those who have free school meals and those who don't.This is the first place I've seen the Return on Investment (ROI) of a biometric system quantified in terms of the uptake in the use of a social program. If the numbers given are accurate, the implementation of an anonymous system for distributing need-based free school lunches can make the difference in whether 30%* of a school's students are getting the nutrition required to give meaning to a school's academic efforts.
Granted, you can shield children from knowing who receives a free meal without using biometrics. Any number of card configurations could manage that. It turns out, however, that card-based solutions among children end up being very expensive in time and money because of lost and forgotten cards.
*30% - assumes nearly all of a schools population qualifies for a free lunch and that there is still a social stigma even when nearly everyone is in the same situation. If only half of the students qualify, which is not uncommon in the United States, the Welsh numbers suggest that 15% more students will eat with an anonymous system than would eat in its absence.
Malaysia is rapidly adopting biometric solutions
Malaysia to use biometric system for voters in elections (MSN - India)
One of the rewarding side effects of keeping this blog is that I end up learning much about the wider world in keeping up with the biometrics news. I'm fond of saying here that biometrics is about people, not technology. Stories like the one below inform that opinion. The ways in which inaccurate identity management plagues well-intentioned systems are extremely numerous and varied.
Biometric system, could assist in tracing runaway maids (Malay Mail)
One of the rewarding side effects of keeping this blog is that I end up learning much about the wider world in keeping up with the biometrics news. I'm fond of saying here that biometrics is about people, not technology. Stories like the one below inform that opinion. The ways in which inaccurate identity management plagues well-intentioned systems are extremely numerous and varied.
Biometric system, could assist in tracing runaway maids (Malay Mail)
Monday, June 20, 2011
It’s Time to Abandon Passwords
Gizmodo.com
For months, there's been a steady trickle of sites getting hacked, followed by their usernames and passwords being passed around publicly on the Web. It's a real and growing problem that's just going to get worse.With the realization that passwords are an obsolete security technology, users are demanding biometrics.
Philippines: Biometrics election registration gets approval
Manila Bulletin
The House of Representatives yesterday gave the nod for the measure requiring biometrics registration for “honest, clean and credible” elections.
Communist Party of India doean't like UID
CPI(Marxist) demands stopping of biometric enrolment (NewKerala.com)
There are several issues which need to be resolved before such an exercise can be undertaken, especially the legal safeguards against misuse and the delinking of social welfare schemes from this exercise, such as access to PDS and MNREGA," Polit Bureau of CPI(M) said in a statement issued here.
Malaysia biometric system enables new citizenship policies
The Star Online
Legalisation of illegal foreign workers from August (MSN India)
For background, see:
6P programme starts on July 11 (Since Delayed)
...also from Malaysia (AsiaOne.com):
The initiative is under the Government's 6P programme which is a large-scale legalisation and amnesty exercise to reduce the number of illegal immigrants in Malaysia.UPDATE: The Amnesty initiative, having been delayed, now rescheduled to begin in August.
Legalisation of illegal foreign workers from August (MSN India)
For background, see:
6P programme starts on July 11 (Since Delayed)
...also from Malaysia (AsiaOne.com):
Yesterday, the immigration clearance at the Causeway and Second Link was back to normal after two weekends of hiccups in the biometric fingerprint scanning system.Hopefully, in another two weeks crossing will be even faster than before.
Friday, June 17, 2011
Access control: Alternative definition
Access control: Selective inefficiency.
No security measure that seeks to allow access to some and prevent access by others can ever be perfect. All a security system can hope to accomplish is to impose a small inefficiency upon those that are allowed access while imposing a large inefficiency upon those that are not permitted access.
As the value of the protected asset increases, larger inefficiencies will be tolerated for those permitted access in exchange for even larger increases in inefficiency for those not permitted access.
No security measure that seeks to allow access to some and prevent access by others can ever be perfect. All a security system can hope to accomplish is to impose a small inefficiency upon those that are allowed access while imposing a large inefficiency upon those that are not permitted access.
As the value of the protected asset increases, larger inefficiencies will be tolerated for those permitted access in exchange for even larger increases in inefficiency for those not permitted access.
Brazilian bank evaluating biometric system for online banking
Bradesco looking into developing device that would identify account holders on the Internet (SecurityInfoWatch.com)
A biometric template by itself isn't enough to gain access.
According to Bradesco executive VP Laercio Albino Cezar, the bank is evaluating developing a device with Fujitsu to identify accountholders on the internet. "We want to create something that isn't integrated into the client computer to use separately, as happens today with the tokens," he was quoted as saying.Mr. Cezar appears to grasp a very subtle point of networked biometric identity management solutions. The hardware is a part of the security. If a hacker steals your banking password, she can just type it into the proper field and she's in. If she steals your unencrypted biometric template (a long character string), she can't just type it in even if she finds the place in the bank's programming that handles the template. In some ways the template is like a password that must come through the sensor.
A biometric template by itself isn't enough to gain access.
Wednesday, June 15, 2011
Web services look to revolutionize biometrics
National Institute of Standards of Technology (NIST) is working to establish protocols to ease implementation and increase interoperability for biometric devices (ThirdFactor.com)
Overcoming the challenges inherent in integrating diverse biometric hardware and software into coherent solutions delivered over multiple platforms is what SecurLinx does.
Currently biometric devices require dedicated software to interact with other electronic devices (e.g. computers, handhelds, mobiles). When either device changes, the wheel must essentially be recreated–or at least the software that drives it. “If devices can understand the Web inherently and the device changes,” explains Micheals, “you don’t have to rely on the software that hinders interoperability.”These protocols will certainly help make our job easier.
Overcoming the challenges inherent in integrating diverse biometric hardware and software into coherent solutions delivered over multiple platforms is what SecurLinx does.
NY hospital implements biometric technology to identify patients
Modality: Palm vein (News-Medical.net)
The advanced technology of PatientSecure helps to ensure each patient is correctly "linked" to the right medical record, a task which is not always as straightforward as it sounds. For example, at the medical center alone, two or more patients share the same first and last names more than 125,000 times.A real tipping point for this industry will be when adopters of biometric ID management solutions begin wringing price reductions out of their insurance companies. Does cutting off the wrong person's leg cost more than a biometric ID system?
Tuesday, June 14, 2011
Your Face as Your Password
From PCWorld
This article gives a consumer's eye view of some of the possibilities and limits of very low cost face rec.
This article gives a consumer's eye view of some of the possibilities and limits of very low cost face rec.
The future has flying cars, replicators, and computers that recognize your face and let you log in just by looking at them. While we may have to wait a bit longer for the cars and the replicators, we can have face recognition right now, and it's surprisingly affordable. I took a look at BioTrust ($13), and it took a look right back at me.
EU ministers back consolidation of population databases
A single agency will be in charge of three EU population-tracking databases under plans approved by EU ministers (OUT-LAW News)
The Council said that a "decisive political agreement" had been reached to back plans for a new agency to be set up by the summer of 2012 to manage the three databases. A proposed regulation drawn up by the European Parliament to establish the new agency receives Ministers' support, the Council said in a statement.
FBI talks about fingerprint information sharing
Biometric Sharing Initiative - Making the World Safer (FBI.gov)
Since 2002, the Global Initiatives Unit has developed relationships with more than 50 countries and has received over 450,000 biometric records that have been added to IAFIS.
Monday, June 13, 2011
Can smart cards curb $370 billion in Medicare fraud?
Politicians eye tech to reduce losses in Medicare, Medicaid (SecureIDNews.com via @m2sys)
With the budget battle underway, the case for a strong identity credential for Medicare may be too good for Congress to pass up. Smart cards could help the federal government to reduce Medicare fraud and abuse to the tune of $370 billion in the next 10-years, says Kelli Emerick, executive director of the Secure ID Coalition.Fraud undermines public faith in social safety nets.
Malaysia Biometrics Update: June 13, 2011
New system ID's wanted terrorist using false name (newKerala.com)
Faster auto travel as Malaysia adds terminals? (AsiaOne.com)
Golfers, others wary (ChannelNewsAsia.com)
"No problem at airports and ports" (Straits Times)
Faster auto travel as Malaysia adds terminals? (AsiaOne.com)
Golfers, others wary (ChannelNewsAsia.com)
"No problem at airports and ports" (Straits Times)
U.S. lacks automated system to track entry and departure of foreign visitors
Houston Chronicle
Nearly a decade after five suicide hijackers with expired U.S. visas helped 14 comrades carry out the Sept. 11 attacks, the Department of Homeland Security and Congress have yet to come up with a fail-safe way to check foreign visitors in and out of the U.S., leaving an unknown number unaccounted for inside the country.Fail-safe? Many would settle for reasonably efficient.
Dr. Bojan Cukic primer on the history of biometric ID
We've posted on Dr. Cukic before.
He's back providing the quotes for a great short synopsis about the history of biometrics.
He's back providing the quotes for a great short synopsis about the history of biometrics.
Friday, June 10, 2011
Biometric Facial Recognition Technology For Jailbroken iPhones
This is cool (Softsailor.com)
Whenever you feel bored with the old way you used to access your iOS device’s screen, download and use the first biometric facial recognition application that is able to work with your native iPhone’s front-facing camera.Biometrics will be far more useful in enhancing privacy than eroding it. Getting low cost biometric tools into the hands of early adopters is very important to the growth of our industry.
European Regulators probe Facebook’s facial recognition
A number of European privacy regulators are investigating Facebook (FT.com)
The issues are often confused. Technology is neither good nor bad. What people do with technology and how they treat each other can be.
So, where are these mounting concerns best directed: facial recognition technology; the Facebook as a technology; or individual decisions by people in positions of power and trust?
This affair has more to do with transparency and consent than any particular technology.
Identity management is about people.
A number of European privacy regulators are investigating Facebook’s facial recognition feature amid mounting concern about the technology, which attempts to identify people in photos uploaded to the website.There is a tension in these two paragraphs. "concern about the technology" or "introducing the feature without permission from users"?
The social networking site has come under fire from the German, UK and Irish authorities for introducing the feature without permission from users.
The issues are often confused. Technology is neither good nor bad. What people do with technology and how they treat each other can be.
So, where are these mounting concerns best directed: facial recognition technology; the Facebook as a technology; or individual decisions by people in positions of power and trust?
This affair has more to do with transparency and consent than any particular technology.
Identity management is about people.
Thursday, June 9, 2011
Facebook Facial Recognition Implementation Raises Privacy Concerns
Face rec software suggests tags for photos uploaded to its site (TECHNEWSWORLD.com)
Facebook has raised concerns among privacy proponents with Tag Suggestions, a new feature that uses facial recognition technology to connect names to faces in uploaded photos and suggest tags to the uploader. Aside from the general privacy worries the feature has spurred, it's somewhat unclear just how long Facebook has had this feature in play.Transparency and Consent. Organizations neglect these at their peril because their customers/users value them highly.
India UID Update: June 9, 2011
Only 5% enrol for Unique ID card in Mumbai (DNAIndia.com)
Now, get UID online (DNAIndia.com)
"We have been given a daily target but how is it possible to meet it if people are not coming forward. A majority of people don't know why UID is important and where to get enrolled. The lapse is both from the vendors' and the civic body's end," said an official from one of the enrollment centres, requesting anonymity.It's not quite as bad as the headline makes it sound. They seem to be missing their goals by about 20% and 5% of Mumbai is a lot of people.
Now, get UID online (DNAIndia.com)
Once operational, citizens will be able to register through a government website and fix suitable appointments at the nearest centre for biometric registration. An official from the IT department of the state government said this will reduce registration time to less than 10 minutes.
Russian Biometric Lie-detecting Robot Bankers
A Russian A.T.M. With an Ear for the Truth (New York Times)
The machine scans a passport, records fingerprints and takes a three-dimensional scan for facial recognition. And it uses voice-analysis software to help assess whether the person is truthfully answering questions that include “Are you employed?” and “At this moment, do you have any other outstanding loans?”As they say, read the whole thing.
Children, Schools, Policy & Technology
Cameras in the toilets; CCTV in the classroom; pupils' fingerprints kept in a database . . . (Manchester Guardian)
The article is an interesting collection of stories from the UK and the US. Taken together they show a picture of schools trying to cope with a whole range of social issues they were not created to address rather than schools acting as the Outer Party of George Orwell's dystopia.
It's worth checking out the comments, too.
The article is an interesting collection of stories from the UK and the US. Taken together they show a picture of schools trying to cope with a whole range of social issues they were not created to address rather than schools acting as the Outer Party of George Orwell's dystopia.
It's worth checking out the comments, too.
Wednesday, June 8, 2011
BIO-Key poll results
BIO-Key International® Releases Survey Results and Comments on Continued Security Breaches (UPDATE: broken link removed)
See also:
Privacy vs Security - A false choice
Unisys Poll: 63% of credit card users would prefer fingerprint
Return on Investment (ROI)
The time has come for every commercial and government enterprise to recognize that traditional methods of security are no longer a deterrent to hackers and cyber thieves. Recent security breaches have proven that tokens are far too vulnerable, especially in cases where the data or information is mission critical and passwords, no matter how sophisticated, are easily compromised.
See also:
Privacy vs Security - A false choice
Unisys Poll: 63% of credit card users would prefer fingerprint
Return on Investment (ROI)
Malaysia roundup
M'sian Minister: We'll solve border jam (AsiaOne - Singapore)
S'poreans unhappy with Causeway fingerprinting (AsiaOne - Singapore)
Sabah Implements Biometric System (Bernama.com - Malaysia)
The press items from Singapore highlight the inconvenience of the new procedures. The press from Malaysia focuses on the societal problems that the new system is expected to help address.
Singapore is, by some measures, the world's busiest port and is essentially a city-state on an island at the tip of the Malay Peninsula. Any change in the border policy of one country will be intensely felt by the other. There is also quite a history between the two countries, to say the least.
Hopefully the future holds a situation where the benefits arising from the important and legitimate needs for travel and commerce between the two countries and are maximized while those vulnerable to mistreatment are protected.
The pressure is on.
See also:
Malaysia Considers Amnesty for Illegal Immigrants (NY Times)
S'poreans unhappy with Causeway fingerprinting (AsiaOne - Singapore)
Sabah Implements Biometric System (Bernama.com - Malaysia)
The press items from Singapore highlight the inconvenience of the new procedures. The press from Malaysia focuses on the societal problems that the new system is expected to help address.
Singapore is, by some measures, the world's busiest port and is essentially a city-state on an island at the tip of the Malay Peninsula. Any change in the border policy of one country will be intensely felt by the other. There is also quite a history between the two countries, to say the least.
Hopefully the future holds a situation where the benefits arising from the important and legitimate needs for travel and commerce between the two countries and are maximized while those vulnerable to mistreatment are protected.
The pressure is on.
See also:
Malaysia Considers Amnesty for Illegal Immigrants (NY Times)
Biometrics for people who can't identify themselves
Georgia police ID comatose suspect by fingerprints (Link Inactive)
More info here (SavannahNow.com)
It looks like the comatose man is a suspect in a crime which (I guess) goes part way to explaining why his family wouldn't ID him. I don't know the law, but can you ID someone to doctors and not the police? It would seem to be extremely risky to the patient's health to withhold critical information, such as medical records which contain identifying information, from the doctors charged with the patient's care.
Stripped of the criminal context, this case is useful in pointing out that there are situations where caregivers and civil servants come into contact with people who are unable to identify themselves. There are many ways various biometric modalities can be used to help.
More info here (SavannahNow.com)
It looks like the comatose man is a suspect in a crime which (I guess) goes part way to explaining why his family wouldn't ID him. I don't know the law, but can you ID someone to doctors and not the police? It would seem to be extremely risky to the patient's health to withhold critical information, such as medical records which contain identifying information, from the doctors charged with the patient's care.
Stripped of the criminal context, this case is useful in pointing out that there are situations where caregivers and civil servants come into contact with people who are unable to identify themselves. There are many ways various biometric modalities can be used to help.
Tuesday, June 7, 2011
IATA Floats Airport Security Revamp
Iata unveils queue-busting airport security prototype (Travolution)
Secure, hassle-free Checkpoint of the Future aims to make air travel 'civilized' (UK Independent)
Passengers should be able to get from kerb to boarding gate with dignity. That means without stopping, stripping or unpacking, and certainly not groping. That is the mission for the Checkpoint of the Future. We must make coordinated investments for civilized flying.
Secure, hassle-free Checkpoint of the Future aims to make air travel 'civilized' (UK Independent)
Today's checkpoint was designed four decades ago to stop hijackers carrying metal weapons," said Bisignani. "Since then, we have grafted on more complex procedures to meet emerging threats. We are more secure, but it is time to rethink everything. We need a process that responds to today's threat.The PDF linked at the bottom of the first article shows that the International Air Transport Association (the industry) gets it.
India UID: Making it stick
No UID, no salary for govt staff (Mid-Day.com)
A government resolution making Unique Identification (UID) card a must for all its employees before the end of the month has left the staff scrambling for forms to complete the enrollment. The Government Railway Police (GRP) and the Pune Municipal Corporation (PMC) have issued circulars to its employees stating their salaries would not be deposited unless they enrolled for the UID card.That'll motivate them.
Monday, June 6, 2011
Understanding the Three Factors of Authentication
InformIT from Pearson Education
Authentication is the first step in access control and there are three common factors used for authentication: something you know, something you have, and something you are. This article provides you with good understanding of the three factors of authentication and how they can be used together with multifactor authentication.
Malaysia Biometric system 'will be fixed'
New Straits Times
There are always a few hiccups when changing security processes.
When Brazil changed its procedures on January 1, 2004, people had to wait up to nine hours. It was so bad that the mayor of Rio hired samba dancers to hand out roses and T-shirts to keep the peace.
Thankfully, countries have learned from Brazil's experience and have gotten better at managing the changes required to implement biometric technologies.
Hishammuddin said he would continue to monitor the situation and share information with countries which had used similar system, adding that the biometric scanning was still at an early stage and needed time to integrate with other existing system.Some people had to wait for 90 minutes in order to get through customs.
There are always a few hiccups when changing security processes.
When Brazil changed its procedures on January 1, 2004, people had to wait up to nine hours. It was so bad that the mayor of Rio hired samba dancers to hand out roses and T-shirts to keep the peace.
Thankfully, countries have learned from Brazil's experience and have gotten better at managing the changes required to implement biometric technologies.
Privacy vs Security - A false choice
Did anyone ever tell you not to flash your cash around in public?
The idea is that showing your roll might attract the attention of would be thieves, pickpockets or muggers.
So in this case keeping your affairs private enhances security. There is no tradeoff.
There are many cases like this. How many of you have heard people say things while on a mobile phone in a public space that would give a malefactor all the information they need to commit a crime with little chance of detection?
How many horrible people have used information about young people they have met online in terrible ways?
We don't value privacy highly because it is the currency with which we purchase security. One of the many reasons we value privacy so highly is that it enhances security even as it is retained.
Now consider the recent data breaches that have led to a loss of privacy and, as a consequence, the reduction of the security of individuals.
Even if the security protocols of the companies involved were weaker than the ones that were actually breached, template-only biometric authentication would provide far more privacy and security than the current username/password regime.
A database including Name, Username, email address and password is far more valuable than one including Name, Username, email address and biometric template. The reasons are somewhat technical, but you can't just type a template into a computer to gain access.
Granted, biometrics are more expensive. But you can trade money for security.
The idea is that showing your roll might attract the attention of would be thieves, pickpockets or muggers.
So in this case keeping your affairs private enhances security. There is no tradeoff.
There are many cases like this. How many of you have heard people say things while on a mobile phone in a public space that would give a malefactor all the information they need to commit a crime with little chance of detection?
How many horrible people have used information about young people they have met online in terrible ways?
We don't value privacy highly because it is the currency with which we purchase security. One of the many reasons we value privacy so highly is that it enhances security even as it is retained.
Now consider the recent data breaches that have led to a loss of privacy and, as a consequence, the reduction of the security of individuals.
Even if the security protocols of the companies involved were weaker than the ones that were actually breached, template-only biometric authentication would provide far more privacy and security than the current username/password regime.
A database including Name, Username, email address and password is far more valuable than one including Name, Username, email address and biometric template. The reasons are somewhat technical, but you can't just type a template into a computer to gain access.
Granted, biometrics are more expensive. But you can trade money for security.
Friday, June 3, 2011
Israel: Biometric ID database to be launched in November
Pilot project will test database (Jerusalem Post)
Reading this article and the one that provided the inspiration for the post linked below, put me in mind of this quote from Israeli Prime Minister Benjamin Netanyahu in his recent address to the U.S. Congress:
See also, Privacy and Security in Israel.
Knesset Science and Technology Committee chairman MK Meir Sheetrit (Kadima) and MK Avraham Michaeli (Shas) both voted in favor of the database at the end of a long discussion in which rights groups opposed the policy on privacy grounds.
Reading this article and the one that provided the inspiration for the post linked below, put me in mind of this quote from Israeli Prime Minister Benjamin Netanyahu in his recent address to the U.S. Congress:
You think you have contentious debates here in Congress? Come visit the Knesset for one day, be my guest.
See also, Privacy and Security in Israel.
Municipal Corporation of Delhi Chief: I ain't afraid of no ghosts
The Municipal Corporation of Delhi Chief doesn't believe in ghosts (Asian Age)
Earlier post on the subject here.
The MCD has told the Delhi high court that there were no ghost employees on its payroll and accused the media of raising a non-existent scam.
Earlier post on the subject here.
It's not the tech, it's the people: Canada & India
In an international version of "it's not about the tech, it's about people"...
Canada appears to be heading for another diplomatic dust-up with India (The Star - Toronto)
I think the author nails it in the concluding paragraphs. I'd also add that, given India's UID project, if the Canadian customs information on Indian citizens is shared back with India, India would be in a position to gain a better picture of how Indian passports are used than China would be if China was in India's place.
Canada appears to be heading for another diplomatic dust-up with India (The Star - Toronto)
That amount is not enough to introduce biometrics in every Canadian overseas mission, so immigration officials are now trying to decide which countries should be first.This really seems to be more about the rivalry between China and India than biometrics.
Security hotspots like Pakistan and Yemen are at the top of the list, but there was room for one large-volume nation as well, according to sources, and India is the recommended choice over China.
The decision could damage relations between Canada and India, which have only recently begun to improve.
I think the author nails it in the concluding paragraphs. I'd also add that, given India's UID project, if the Canadian customs information on Indian citizens is shared back with India, India would be in a position to gain a better picture of how Indian passports are used than China would be if China was in India's place.
L-1 Identity says US begins 45-day probe of Safran deal
[Reuters] L-1 Identity Solutions Inc said the Committee on Foreign Investment in the United States (CFIUS) was investigating the face-recognition software maker's sale to French defense company Safran.L-1 is much more than a "face-recognition software" maker.
Thursday, June 2, 2011
Privacy Leadership: What it Takes
Those anxiously awaiting the next installment of our privacy series, might find this interesting.
Today's Threats Require a New Breed of Privacy Officer (GovInfoSecurity.com) via @heidishey
Today's Threats Require a New Breed of Privacy Officer (GovInfoSecurity.com) via @heidishey
"Privacy's focus is increasingly on transparency now," Herath says. "This is fundamentally creating new challenges for professionals in their approach toward privacy and data protection."
For instance, the new generation of workers blurs the lines of personal and professional communication in their use of social media, and the type of information that is collected by these sites is often not in the control of an organization. Moreover, it can be used to cause reputational or fraudulent damages.
Australia National Security Science and Technology department plans public outreach
NSST aims to tackle biometric bogeyman perceptions (Computerworld.com.au)
A government organisation that funds biometrics projects, such as tracking large groups of people congregating in one area, is planning to reach out to the community to lessen fears about biometric technology.
Speaking at the A/NZ Biometrics Institute conference in Sydney, Dr Helen Cartledge, told delegates that the National Security Science and Technology (NSST) wants community input in order to improve the perception of biometrics in Australia and also make policy changes.
India: Biometrics curb corruption and help the poor
Curbing Corruption (Times of India)
Helping the Poor (Deccan Herald)
UPDATE
...and more corruption (Times of India)
Sources said that the department was left with no other option as it has failed to achieve the expected attendance outcome, even after conducting frequent raids in various government schools during the past six months.
Helping the Poor (Deccan Herald)
Currently, funds under these schemes are disbursed through post offices or co-operative banks. The beneficiaries were facing difficulties in accessing their branches, which are mostly situated in talukas.
UPDATE
...and more corruption (Times of India)
Jaiswal issued suspension orders of these health employees following a series of complaints received from NMC health committee chairperson Alka Dalal. She has many times pointed out that although the biometric machines installed at various zones have brought down proxy attendance since the workers have to be physically present, they continue to remain missing in their wards during work hours and are only seen at the ward offices at the designated time to mark their in-out time.
Canadian border guards want face rec
Border workers push for biometric screening (CTV News)
That, however, doesn't make it useless. It is a valuable tool in the hands of trained personnel.
Computers don't look at the world the way we do. Whether that's a good thing or not depends on what you're trying to accomplish. For facial recognition in a law enforcement context, it's a good thing to have a radically different point of view applied to a challenge.
First, faces are probably the most meaningful objects in human existence. It's not too much of an exaggeration to say that for millennia human survival has depended upon our abilities at one type of facial recognition: recognizing people you know. Sorting through hundreds of thousands of pictures of people we don't know in order to match the two that are of the same person, however is not something we're inherently good at.
Computers can do that in less than a second, then give the two pictures to a human which is very good at making the single comparison.
The computer does this by treating the face as a mathematical formula. It finds the eyes, then the nose, then other points, measures the distances and angles between the points and turns that all into a long number. Then it does that for everyone in the database. Then it just compares numbers to see which ones come close to matching. It doesn't care about age, race, or gender. It'll match a white man and a black woman. It will match a picture of an old person taken one year ago with a picture of a young person taken today (i.e. a match that's impossible because people don't get younger).
People don't do that. When you ask a person to describe someone they're likely to tell you they were Hispanic, middle aged, round faced, good looking, brown eyes, etc. The computer says: Their eyes were 57.55 mm apart; tip of nose 25 mm below that line 2mm off center to the left, etc.
People and Face Rec make a good team because it's hard to fool them both at the same time. People can't memorize the faces of 1000's of people they don't know & you can fool them by cross-dressing or disguising yourself as a much older person. Computers don't know anything about gender, ethnicity, age or attractiveness, but they can do the math on 1000's of faces in an instant.
Canada's front-line border officers back the idea of a perimeter security arrangement with the United States, with a few caveats.Facial recognition often gets knocked around a bit because casual observers think it is supposed to function well as an unattended system. Maybe one day it will, but not yet.
The Customs and Immigration Union wants more intensive screening of travelers, including a biometric face-recognition tool to pinpoint security threats and wanted criminals.
That, however, doesn't make it useless. It is a valuable tool in the hands of trained personnel.
Computers don't look at the world the way we do. Whether that's a good thing or not depends on what you're trying to accomplish. For facial recognition in a law enforcement context, it's a good thing to have a radically different point of view applied to a challenge.
First, faces are probably the most meaningful objects in human existence. It's not too much of an exaggeration to say that for millennia human survival has depended upon our abilities at one type of facial recognition: recognizing people you know. Sorting through hundreds of thousands of pictures of people we don't know in order to match the two that are of the same person, however is not something we're inherently good at.
Computers can do that in less than a second, then give the two pictures to a human which is very good at making the single comparison.
The computer does this by treating the face as a mathematical formula. It finds the eyes, then the nose, then other points, measures the distances and angles between the points and turns that all into a long number. Then it does that for everyone in the database. Then it just compares numbers to see which ones come close to matching. It doesn't care about age, race, or gender. It'll match a white man and a black woman. It will match a picture of an old person taken one year ago with a picture of a young person taken today (i.e. a match that's impossible because people don't get younger).
People don't do that. When you ask a person to describe someone they're likely to tell you they were Hispanic, middle aged, round faced, good looking, brown eyes, etc. The computer says: Their eyes were 57.55 mm apart; tip of nose 25 mm below that line 2mm off center to the left, etc.
People and Face Rec make a good team because it's hard to fool them both at the same time. People can't memorize the faces of 1000's of people they don't know & you can fool them by cross-dressing or disguising yourself as a much older person. Computers don't know anything about gender, ethnicity, age or attractiveness, but they can do the math on 1000's of faces in an instant.
Malaysia Biometric system in force at all entry points
The Star/Asia News Network
The National Foreigners Enforcement and Registration System was introduced yesterday without any major hiccups.
Deputy Home Minister Datuk Wira Abu Seman Yusof said foreigners entering the country would now have their thumbprints taken electronically.
"The process went on smoothly and the department has not received any complaints so far.
"However, the system is new and there are bound to be minor glitches," he told The Star.
Subscribe to:
Comments (Atom)